 Palo Alto Networks is focused on the $7.4bn network security market. Specifically, Palo Alto is a vendor of NGFWs – Next Generation Firewalls a part of Unified Threat Management (UTM) devices, the fastest growth segment of the network security market. Palo Alto is a startup in the Enterprise Security space with revenue of just $166mn in 2011.
Palo Alto Networks is focused on the $7.4bn network security market. Specifically, Palo Alto is a vendor of NGFWs – Next Generation Firewalls a part of Unified Threat Management (UTM) devices, the fastest growth segment of the network security market. Palo Alto is a startup in the Enterprise Security space with revenue of just $166mn in 2011.
Check Point and Fortinet are two big names in the UTM segment. The addition of yet another function to their UTM appliances has hurt the performance of these solutions. Indeed, these appliances began with a stateful inspection firewall and continued to add performance-degrading functions in series behind the key firewall function. This is where Palo Alto’s unique single-pass architecture performs all security functions in parallel, rather than in series. This reduces degradation, providing improved performance and has gained acceptance in the market place.
Palo Alto is the key beneficiary of the presence of Web 2.0 technologies [Facebook, Twitter, Skype, LinkedIn, etc] seeing increasing adoption in the enterprise. With increasing pressure from employees, corporate managements want to let employees use Social Network and other Web 2.0 technologies, responsibly; for instance allow employees to send and read Facebook messages but block Games and Apps such as farmville. The company has the advantage of having one of the newest products on the market and thus a more modern architecture than its competitors.
Palo Alto’s appliances use three key identification technologies to provide their NGFW solution: App-ID, User-ID, and Content-ID. 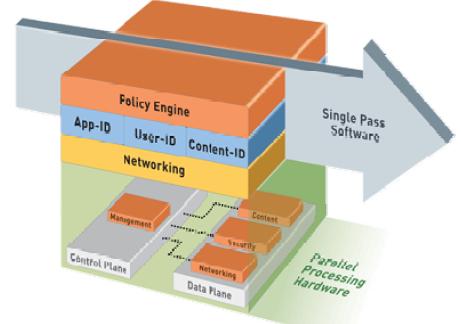
App Id App-ID is the technology that Palo Alto uses to identify which applications are being accessed by users. Palo Alto’s App-ID can determine the identity of more than 1,500 applications. Once the identity of the application is determined, then, based on policies set by the user’s IT department, the appliance either blocks the application or allows it and then checks it for threats or unauthorized file transfers.
User Id User-ID is the technology that Palo Alto uses to identify which user is accessing certain applications and what rights this user has. Palo Alto can base these policies around individuals, groups, or departments. For example, the management decides that there is a business case for those in the sales department to have access to social networking sites but that those in the engineering department should be blocked from accessing these sites at work.
Content-ID Content-ID is the technology that Palo Alto uses to identify potential threats within applications that are permitted. Content-ID scans acceptable applications for threats, such as viruses, as well as potential data leakage. It also performs URL filtering so that IT administrators can monitor and control which sites users are surfing.
How Palo Alto’s Single-Pass Parallel Processing Architecture is Superior ?
UTM appliances have evolved over time, adding technology in series with previous technology as new threats and demands emerge. Check Point’s appliances, for instance, have many different functions that traffic is put through in series (e.g., firewall, URL filtering, antivirus, application control). Palo Alto’s appliance was initially designed with an understanding that it would have to perform many functions and that it should perform these functions with as little performance degradation as possible to the user.
This Single Pass Parallel Processing – SP3 architecture scans network traffic once and performs all analysis in this one pass. This reduces latency issues, as the traffic is inspected just one time, rather than multiple inspections with traffic being passed from scan to scan.
1 thought on “An Insight into Palo Alto Single Pass Architecture for NGFW for Controlled Corporate Network Access”
Comments are closed.